
A U.S. sailor reviews a map aboard the Ticonderoga-class guided-missile cruiser USS Cape St. George (CG 71), July 28, 2012. U.S. Navy photo by Mass Communication Specialist 3rd Class Christopher S. Johnson
Congress Will Rethink Combatant Command Boundaries
Reshaping, or even deleting, some of the four-star headquarters that run America’s military operations around the world could be part of broader Defense Department reforms.
Congress may reshape — or even close — some of the Pentagon’s combatant commands, the four-star headquarters that oversee military activities in all corners of the world, the Senate Armed Services Committee chairman said Thursday.
Sen. John McCain, R-Ariz., said his panel would look at combatant command responsibilities when it considers broader Defense Department reforms this year.
“We need to figure out whether we need the ones that we have,” McCain said at a Defense Writers Group breakfast.
The boundaries of what the military calls “COCOMs” are laid out in a document called the Unified Command Plan . Every few years, defense leaders debate redrawing the boundaries or combining commands , but there haven’t been any major changes since U.S. Africa Command was created in 2006.
In 2012 and 2013, Pentagon leaders considered combining U.S. Northern Command, which oversees homeland defense of the continental United States, Canada and Mexico, with Southern Command, which oversees Central and South America. And in December, incoming Joint Chiefs Chairman Gen. Joseph Dunford said he’d be open to changes.
McCain on Tuesday hinted that lawmakers would consider combining those two commands.
“We need to look at small things, such as ‘Do we need a NORTHCOM and a SOUTHCOM?,” he said. “Why should there be an arbitrary line at the Mexico-Guatemala border?”
As well, the structure of Africa Command, which is headquartered in Europe, has been debated since its creation.
“Is it right for us to have an Africa [Command] headquarters in Stuttgart, Germany?,” McCain said. “Is that what we had in mind when we formed up AFRICOM?”
Some have argued that Northern Command should oversee all military action in the Arctic, where nations are jockeying for natural resources. NORTHCOM currently splits the responsibility with European Command.
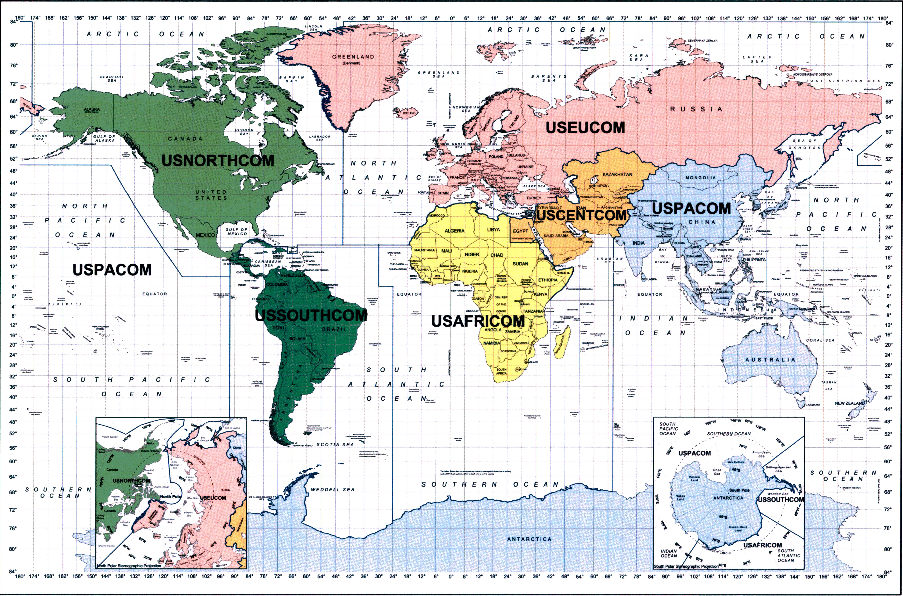
Defense Department
map
, labeled, "The World With Commanders' Areas of Responsibility."
