The biggest cyber threats: spies, criminals or co-workers?
Verizon's 2014 report finds malicious threats are on the rise, but so are common mistakes.
State-sponsored cyber espionage rose sharply in 2013 and attacks on Web applications are always a concern, but the most common threat to government networks and data comes from the inside, often the result of accidents, according to Verizon’s 2014 Data Breach Investigations Report.
Verizon reviewed 63,437 cybersecurity incidents and 1,367 confirmed data breaches for this year’s report, and found that 26 percent of the incidents resulted from what the report categorized as “miscellaneous errors,” in which unintentional actions directly compromise security. Common culprits include emailing a document to the wrong person or accidentally publishing information on a website.
And government was the culprit in the majority of those errors, although the numbers are inflated by mandatory reporting requirements. “According to our sample, government organizations frequently deliver non-public information to the wrong recipient,” the report states. However, the report notes that the U.S. government handles a lot of information and requires reporting on even mundane incidents that aren’t necessarily required by other sectors.
Fifty public and private organizations, with a presence in a total of 95 countries, contributed to the report, including US-CERT, the Defense Security Service, the Secret Service and the Homeland Security Department's National Cybersecurity and Integration Center.
Overall, the report found that crimeware accounted for the second most incidents, at 20 percent, followed by intentional insider misuse (18 percent) and physical theft/loss (14 percent). Among data breaches, Web app attacks led with way, accounting for 35 percent of breaches, followed by two categories that were barely a blip in the number of total incidents but tended to get results: cyber espionage (1 percent of incidents, 22 percent of breaches) and point-of-sale intrusions (less than 1 percent of incidents, 31 percent of breaches). In fact, breaches occurred in all 198 POS incidents. (The Target hack is the most well-known of this type of attack, although Verizon scrubs its data of victims’ identities.)
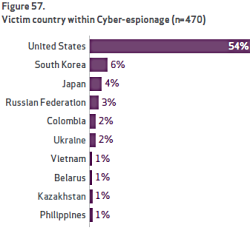
And although cyber espionage accounted for a small number of incidents in the report, that number tripled from 2012. State-affiliated attacks accounted for 87 percent of all cyber espionage, followed by organized crime at 11 percent. The United States was by far the top target of cyber espionage, being hit by 54 percent of the attacks, followed by South Korea (6 percent), Japan (4 percent) and Russia (3 percent).
And even within the cyber espionage category, attacks still often turn on a user error. Email attachments were the vector in 78 percent of attacks, according to the report, which reflects other reports that phishing is the top method used in targeting government. Drive-by Web attacks were the second most common vector, at 20 percent, followed by direct install (4 percent), downloaded malware (3 percent) and an email link (2 percent).
The report, which Verizon has been doing annually for a decade, also offers a 10-year overview of cybersecurity, and found that 92 percent of the more than 100,000 incidents reviewed can be attributed to one of nine basic patterns: miscellaneous errors, crimeware, insider/privilege misuse, physical theft/loss, Web app attacks, denial of service attacks, cyber espionage, point-of-sale intrusions and payment card skimmers.



