What the NSA’s Massive Org Chart (Probably) Looks Like
Amid public cries for greater transparency into the intelligence world, here’s a look at the National Security Agency’s organizational chart -- as far as we know it. By Marc Ambinder
Want to understand how an organism really works? Take a look at its plumbing. Figure out where the pipes fit together. That’s the approach I take to national security and that’s the spirit behind this look at the structure of one of the most important institutions in U.S. intelligence: the National Security Agency.
Some intelligence organizations, such as the National Reconnaissance Office and the National Geospatial Intelligence Agency, have declassified most of their organizational charts. The NRO develops, launches and controls spy satellites; the NGA analyzes and distribute imagery. For these agencies, the plumbing matters less than what flows through the pipes, which is highly classified.
But the NSA, with its triple mission -- break codes, secure data, collect signals intelligence -- has not made its structure public. Even by the standards of U.S. intelligence agencies whose existence was declassified much later, the NSA’s organization chart is largely impermeable to outsiders. The best of its chroniclers, like Jeff Richelson, James Bamford, Bill Arkin and Matthew Aid, have managed to collect bits and pieces of open source data, but many senior intelligence officials who don't work for NSA still have only a vague idea of what signals intelligence collection entails, and even fewer understand the NSA bureaucracy. The map to the NSA's inner sanctum is generally given only to a select few members of Congress and their staff.
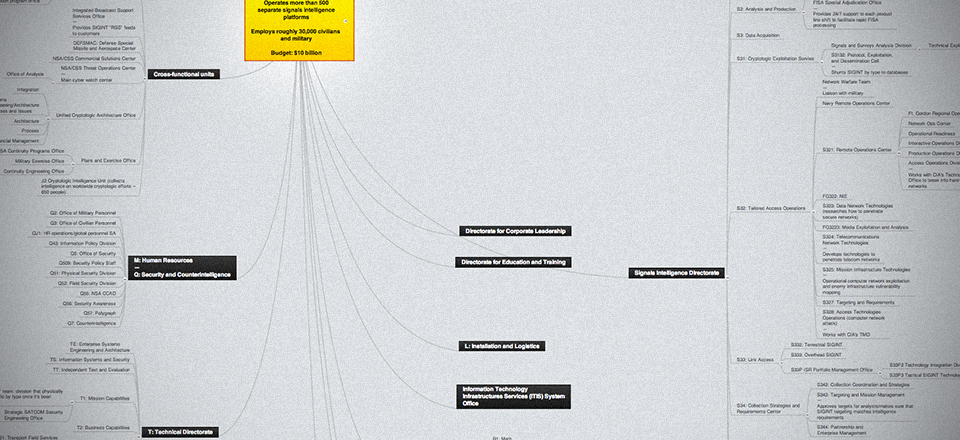
In the interests of transparency and in an effort to establish a basis for continued public exploration of the world of intelligence, I’ve cobbled together a rough and incomplete but still rather comprehensive organizational chart of the agency’s operational, analytical, research and technology directorates. With only a few exceptions, the information does not come from inside sources. It builds on the work of the researchers mentioned above and it represents the culmination of a lot of time spent cross-checking government documents and LinkedIn profiles, job postings and agency announcements.
The NSA prefers not to discuss how it works and what it does. Defense One offered NSA the opportunity to review the organization chart and address any national security concerns. "We won't fact check a chart that appears to be based largely on speculation," the agency replied through a spokesperson.
Undoubtedly, some of what follows is incomplete and I hope knowledgeable readers will set me straight.
Click through the image below to enter a mind map in which readers can explore the far-reaching branches of NSA’s organizational structure:
It has five operational directorates, several administrative directorates and three large operational centers. Each is headed by an associate director, and each associate director has a technical director. They report to the executive director, who reports to the deputy director, who reports to the DIRNSA, which is NSA-speak for Director of the NSA, Gen. Keith Alexander. He’s also the commander of the Defense Department’s U.S. Cyber Command and the Central Security Service, the military signals and cyber intelligence units that contribute personnel to the NSA. The CSS is essentially the NSA.
The NSA’s Foreign Affairs Directorate interacts with foreign intelligence services, counterintelligence centers and the UK/USA and FIVE EYES exchanges, an alliance of intelligence operations between the U.S., UK, Canada, Australia and New Zealand that dates back to 1946. It also includes the Office of Export Control Policy.
The Information Assurance Directorate is the center of NSA’s cyber warfare and defense program offices. It’s also responsible for generating the codes that the U.S. uses.
The Signals Intelligence Directorate is the largest functional directorate. It has three subdivisions. One helps determine the requirements of what the NSA calls its customers -- other agencies, the president, the military. The agency’s main analytical centers live here, too. The super-secret work of SIGINT collecting and offensive cyber warfare is the responsibility of S3, with its many bland sounding and compartmentalized branches.
The Research Directorate figures out how to break codes and how to best penetrate the telecom infrastructure of tomorrow. The Technical Directorate puts everything together. It’s responsible for the infrastructure for everything NSA does.
Two other directorates are responsible for training and human resources and for acquisition and procurement.
The NSA’s three operational centers are its main watch facility, the National Security Operations Center, or NSOC; the National Threat Operations Center, which is the U.S. government’s primary worldwide cybersecurity warning office; and the NSA/CSS Commercial Solutions center, which interacts with private companies, uses commercial technologies for classified purposes and conducts research on cryptography that the government is willing to share with the public.
Another NSA office is the Special Collection Service, which is run jointly with the CIA and operates classified listening posts from embassies and other special facilities worldwide. The SCS is responsible for NSA listening posts that aren’t inside of U.S. or allied military facilities.
Inside the United States, the NSA has very large off-site campuses in Hawaii, Texas, Utah and Georgia. In Maryland, it owns and hosts offices in Linthicum, Finksberg, Bowie and College Park, alongside Ft. Meade, its home, and adjacent properties. There’s an NSA office inside the Cheyenne Mountain Operations Center, where NORAD and NORTHCOM have their backup command center. And NSA has a big presence at Site R, the site of the Alternate National Military Command Center, near Ft. Ritchie, Md.
[Related: The NSA's New Spy Facilities are 7 Times Bigger Than the Pentagon ]
All these sites are connected by an architecture called NSANet, which exists in parallel to the regular telephone switch system. Real-time feeds of SIGINT reports and time-sensitive cyber information can be sent to users anywhere in the world, such as those on Navy ships, using the NSA’s Integrated Broadcast Service.
The NSA uses a bewildering amount of technical tools and databases. You’ve now heard of PRISM, which was revealed in the Edward Snowden leaks. This system collects digital network information from U.S. content providers.
The NSA also has several tools and databases, including metadata collection, a repository of malicious network signatures and an Air Force/Navy tool that tracks ships in real time.
Here are the other main NSA collection tools and databases:
ONEROOF: Main tactical SIGINT database (Afghanistan), consisting of raw and unfiltered intercepts
NUCLEON: Global telephone content database
XKEYSCORE: Collection tool for international metadata
AIRGAP: Priority missions tool used to determine SIGINT gaps
HOMEBASE: Tactical tasking tool for digital network identification
SNORT: Repository of computer network attack techniques/coding
WIRESHARK: Repository of malicious network signatures
TRAFFICTHIEF: Raw SIGINT viewer for data analysis
BANYAN: NSA tactical geospatial correlation database
OILSTOCK: Air Force/Navy tool to track ships in real time
MAINWAY: Telephony metadata collection database
ASSOCIATION: Tactical SIGINT social network database
MESSIAH/WHAMI: Electronic intelligence processing and analytical database
MARINA: Internet metadata collection database
PINWALE: Internet data content database
SURREY: Main NSA requirements database, where targets and selectors are “validated” by NSA managers
PROTON: SIGINT database for time-sensitive targets/counterintelligence
OCTAVE/CONTRAOCTAVE: Collection mission tasking tool
WRANGLER: Electronic intelligence intercept raw database
ANCHORY: Main repository of finished NSA SIGINT reports going back three years.
AQUADOR: Merchant ship tracking tool
So how do you get NSA to spy on someone? You send in an IN. An IN is an Information Need. The INs go into the collection requirements databases, like SURREY, and are evaluated. Are they time-sensitive? Are they critical, meaning intel is needed within three days? Do they fit in with the National Intelligence Priority Framework, which lays out in broad terms the targets the NSA is working on in any given year?
To invert a phrase from biology, in the intelligence community, function follows form. To begin to understand the NSA from the outside, you need to understand what it looks like from the inside.