Is the CIA Ready for the Age of Cyberwar?
Behind the most sweeping reforms in the agency’s history—and their limits
When America goes to the polls on November 8, according to current and former U.S. intelligence officials, it will likely experience the culmination of a new form of information war. A months-long campaign backed by the Russian government to undermine the credibility of the U.S. presidential election—through hacking, cyberattacks, and disinformation campaigns—is likely to peak on voting day, the officials said.
Russian officials deny any such effort. But current and former U.S. officials warn that hackers could post fictional evidence online of widespread voter fraud, release a final tranche of embarrassing hacked emails, and slow the internet to a crawl through cyberattacks.
“Don’t underestimate what they can do or will do. We have to be prepared,” Leon Panetta, who served as Central Intelligence Agency director and defense secretary in President Barack Obama’s first term, told me. “In some ways, they are succeeding at disrupting our process. Until they pay a price, they will keep doing it.”
John Brennan, the current CIA director, declined to comment on the Russian efforts. But he said Russian intelligence operatives have a long history of marrying traditional espionage with advances in technology. More broadly, Brennan told me, the digital age creates enormous opportunities for espionage. But it also creates vulnerabilities.
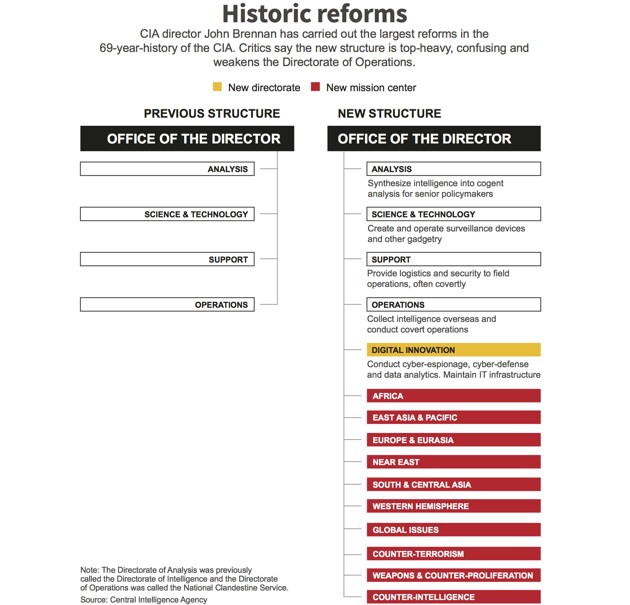
Citing an array of new cyber, conventional, and terrorist threats, Brennan announced the most sweeping reforms of the CIA in its 69-year history 18 months ago. Weakening the role of the Directorate of Operations, the agency’s long-dominant arm responsible for gathering intelligence and conducting covert operations, Brennan created 10 new “mission centers” where CIA spies, analysts, and hackers work in teams focused on specific issues. He also created a new Directorate for Digital Innovation to maximize the agency’s use of technology, data analytics, and online spying.
The information age “has totally transformed the way we are able to operate and need to operate,” Brennan said in a series of interviews. “Most human interactions take place in that digital domain. So the intelligence profession needs to flourish in that domain. It cannot avoid it.”
When a new American diplomat arrives for duty at the U.S. embassy in Moscow or Beijing, CIA officials say, Russian and Chinese intelligence operatives run data analytics programs that check the “digital dust” associated with his or her name. If the newcomer’s footprint in that dust—social-media posts, cell phone calls, debit card payments—is too small, the “diplomat” is flagged as an undercover CIA officer.
The Russian-backed campaign to discredit the U.S. election is not isolated. Hackers believed to have links to Chinese intelligence began stealing the personnel records of 21.5 million federal employees and job applicants in 2014, the worst known data breach in U.S. government history. Islamic State propagandists online continue to inspire lone-wolf attacks in the United States even as the group loses territory.
James Clapper, the Director of National Intelligence, praised Brennan and his efforts to retool the CIA for this new digital era in an interview. So did Lisa Monaco, Brennan’s successor as Obama’s homeland security and counterterrorism adviser.
But some current and former officials question Brennan’s strategy, arguing his reforms are too digitally focused and will create a more cautious, top-heavy spy agency. At a time when the agency needs to refocus its efforts on human espionage, they say, the concentration of power in the new mission centers weakens the ability of the Directorate of Operations to produce a new generation of elite American spies.
Glenn Carle, a former CIA covert officer, praised Brennan and his reforms but said they have sparked a mixed reaction among Directorate of Operations officials who believe human intelligence is getting short shrift. “The value the CIA can fundamentally add is to steal secrets, and the ultimate secret is intention,” Carle said, referring to the often inscrutable aims of foreign leaders. “Obtaining that is a human endeavor.”
Reuters
At the same time, Brennan has stirred a different sort of criticism—that he has defied congressional oversight. Liberal Democrats and libertarian Republicans in Congress say the Brennan-Obama tenure has been tarnished by a lack of transparency with congressional oversight committees and the public regarding surveillance, drone strikes, and the agency’s use of torture against terrorism suspects during the administration of George W. Bush.
“While I think John’s overall legacy will be as a reformer, that legacy will suffer from his refusal to come to grips with the CIA’s troubled torture program,” said Senator Dianne Feinstein, a California Democrat and vice chair of the Senate’s intelligence committee. “I think the new president's CIA director must prioritize a high level of trust between the CIA and Congress to insure proper oversight is conducted.”
It’s unclear how closely the country’s next president will hew to Brennan’s strategy. The front-runner, Democrat Hillary Clinton, has an incentive to beef up American cyberespionage: U.S. intelligence officials blame the continuing leak of emails from her campaign on Russian-backed hacking. Clinton also expressed support for covert action in a transcript of a 2013 speech she gave to Goldman Sachs that was recently released by Wikileaks.
Republican Donald Trump, meanwhile, pledged to make cybersecurity a top priority in his administration in an October 3 speech. “For non-state terror actors, the United States must develop the ability—no matter how difficult—to track down and incapacitate those responsible and do it rapidly,” Trump said. “We should turn cyberwarfare into one of our greatest weapons against the terrorists.”
In interviews at agency headquarters in Langley, Virginia, Brennan declined to comment on either candidate or discuss operational details of the CIA. But he and eight other senior CIA officials gave the most detailed description yet of their rationale for the most radical revamp of the agency since its founding in 1947. “I look out at the next 10, 20, 30 years, and I look at technology, I look at complexity, I look at the global environment,” Brennan said. “I think CIA really needs to up its game.”
Today, Brennan says the United States faces the most complex array of threats he has seen since joining the agency 36 years ago. As a CIA analyst, operative, and executive, he lived the Cold War espionage duels of the 1980s; the disintegration of nation states after the 1989 fall of the Berlin Wall; the rise of non-state terrorist groups since 2001; and the current digital disruption. Now, he says, all four dynamics are converging at once.
CIA officials told me their greatest state competitors are the Russian and Chinese intelligence services. While smaller countries or terrorist groups may want to strike at the United States, Russia and China are the only two adversaries with the combination of skills, resources, and motivation needed to challenge Washington.
In recent years, Moscow’s Federal Security Service, or FSB, has become adept at waging “gray zone” conflicts in Ukraine, Crimea, and Syria, the officials said. In all three countries, Russian intelligence operatives have deftly shrouded protagonists, objectives and war crimes in ambiguity.
One target is America’s increasingly politically polarized democracy. As Russian-backed hacking unfolded this summer, the Obama White House’s response fueled frustration among law-enforcement and intelligence officials, according to current and former officials. The administration, they said, seemed to have no clear policy for how to respond to a new form of information warfare with no rules, norms or, it seemed, limits.
Read more from our series Rethinking Intelligence, a co-production of Defense One and the Brennan Center for Justice
White House officials said the administration is still considering various methods of responding, but the responses won’t necessarily be made public.
China presents another challenge. Chinese businessmen and students continue trying to scoop up American state and economic secrets. In one bright spot, Beijing appears to be abiding by a 2015 pact signed by Obama and Chinese leader Xi Jinping that the two governments would not conduct economic espionage against one another. Chinese cyberattacks appear to have slowed from the voracious rate of the past, which included hacking into the computers of the 2008 presidential campaigns of John McCain and Barack Obama but not releasing what was found.
“The question is whether or not it is due to greater care in terms of covering one’s tracks,” Brennan said of the apparent change. “Or whether or not they realize that their brand is being tarnished by this very rapacious appetite for vacuuming up things.”
In a 2015 case, federal prosecutors indicted a 20-year-old hacker from Kosovo. With the help of a criminal hacker, Ardit Ferizi stole the home addresses of 1,300 members of the U.S. military, providing the information to Islamic State and posting it online, and calling for attacks on the individuals. Ferizi was arrested in Malaysia, where he was studying computer science. In September, Ferizi pleaded guilty in a U.S. federal court and was sentenced to 20 years in prison.
“This blend of the criminal actor, the nation-state actor, and the terrorist actor, that’s going to be the trend over the next five years,” said John Carlin, who recently stepped down as head of the Justice Department division that monitors foreign espionage in the United States.
But some active clandestine officers argue that the intelligence community has grown too reliant on technology, a trend they trace back four decades to the directorship of Stansfield Turner. Satellite photography, remote sensors, and communications intercepts have become more sophisticated, but so have encryption techniques and anti-satellite weapons.
More important, they argue, is that technology is no substitute for “penetrations” —planting or recruiting human spies in foreign halls of power. The CIA missed India’s 1998 nuclear tests and misjudged Saddam Hussein’s arsenal in 2003 because it lacked spies in the right places.
Some former officials question Brennan’s strategy, arguing his reforms are too digitally focused and will create a more cautious, micromanaged spy agency. At a time when the agency needs to refocus its efforts on human espionage, they say, the centering of power in the new mission centers weakens the ability of the Directorate of Operations to produce a new generation of elite American spies who can take risks in the field.
Today, these current and former CIA officials contend, American policymakers have little insight, for example, into the thinking of Vladimir Putin’s inner circle. Presidents, kings, and dictators often don’t share their private thoughts and true intentions electronically, putting this invaluable information largely beyond the scope of digital spying. The best sources are still people, and these officials believe the agency is not mounting the kind of bold human spying operations it did in the past.
Brennan and other CIA officials flatly denied downplaying human intelligence. They said aggressive, high-risk human spying is under way, but they cannot go into operational detail.
One of Brennan’s predecessors, Michael Hayden, a former CIA chief under President George W. Bush, says the agency strayed from its core mission during the Bush years. After the al-Qaeda attacks of Sept. 11, 2001, the CIA had to shift to become more of a paramilitary organization that devoted its most talented officers to tracking and killing terrorists. It now needs to reverse that trend by again focusing on espionage against rival nations, he said.
“The constant combat of the last 15 years has pushed the expertise of the case officer in the direction of the battlefield and in the direction of collecting intelligence to create physical effects,” said Hayden, using an intelligence euphemism for killing. “At the expense of what the old guys called long-range, country-on-country intelligence gathering.”
Richard Blee, a former CIA clandestine officer, said the agency needed reform but highlighted a separate problem created by technological change. Instant secure communications between CIA headquarters and officers in the field has centralized decision-making in Washington, Blee said. And regardless of administration, senior officials in Washington are less willing to take a risk than field officers—virtually all of whom complain about headquarters’ excessive caution.
“The mentality across the board in Washington is to take the lowest common denominator, the easiest option, the risk-free option,” he said. “The Chinese are taking tough decisions, the Russians are taking tough decisions, and we are taking risk-averse decisions. And we are going to pay a price for that down the road.”
Brennan says his reforms will empower CIA officers: The integrated teams in each new mission center will improve speed, adaptability and effectiveness. The old ways of spycraft, he argues, are no longer tenable. Asked what worries him most, he gave a technocratic answer: Twentieth-century American government management practices are being rendered obsolete in the digital age.
“U.S. decision-making processes need to be streamlined and accelerated,” he said. “Because the problems are not going to wait for traditional discussions.”
This post appears courtesy of Reuters.




