Tiny components could help secure the IT supply chain
DARPA awards a $4.1 million contract under its SHIELD program to detect counterfeit parts.
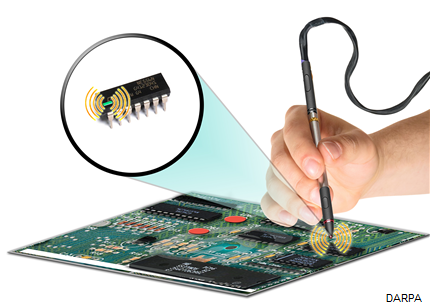
Military researchers are moving ahead with their plan to protect the IT supply chain with tiny, inexpensive components, known as dielets, that can be added to electronics parts to validate their authenticity.
The Defense Advanced Research Projects Agency has awarded a $4.1 million contract to Charles Stark Draper Laboratory of Cambridge, Mass., to develop the dielets, under DARPA’s Supply Chain Hardware Integrity for Electronics Defense, or SHIELD, program.
The agency first issued a solicitation for the program in February 2014, citing the ongoing problems the Defense Department has with counterfeit parts. A faulty microchip, for example, could disrupt an entire system, putting warfighters’ lives at risk. Over a two-year period, the Senate Armed Services Committee found more than 1 million counterfeit parts in the supply chain.
Under the contract, Draper Lab researchers will develop 100-by-100-micron dielets—about a tenth the size of a pencil tip—that can be added to components without affecting their design or functionality. The dielets, attached at a manufacturing site or added to other trusted parts, won’t have an electronic connection to the components, but will have a full encryption engine and sensors to detect tampering, such as revealing an exposure to light.
Scans could be done with a handheld probe or a larger, automated device for large volumes of products. After a scan, a device such as a smartphone would send an unencrypted challenge to the dielet, which would respond with an encrypted answer. The response would include data from its sensors that could indicate tampering, DARPA said.
“SHIELD demands a tool that costs less than a penny per unit, yet makes counterfeiting too expensive and technically difficult to do,” Kerry Bernstein, DARPA program manager, said when the program was announced. “The dielet will be designed to be robust in operation, yet fragile in the face of tampering. What SHIELD is seeking is a very advanced piece of hardware that will offer an on-demand authentication method never before available to the supply chain.”
The program intends to provide protection against recycled, unlicensed and substandard components, parts with fraudulently labeled reliability or manufacture dates, clones or copies that could have hidden functionality, and covertly repackaged parts that could contain unauthorized applications.